
25 posts
Posted 12 March 2013 - 01:03 PM
Computer Protector V1.0.0
[left]Computer Protector is a program I made for a server I am at. In the server we have "computer labs" where users can use the public computers. The problem is, we don't want them installing malicious scripts, so I create a program that requires the users to: [/left]
- Have a Disk Drive
- Have a Disk in said Driver
[left]
The program is basically a virtual sandbox of the computer. Data can only be accessed/written to the floppy disk. In fact, you can only access the floppy disk folder. Thus, you don't save data to the computers in the computer lab(such as key loggers).[/left]
[left]
I need to have a few people try to bypass the code and delete the startup file. Note: You have to do it by code, no driver on the top of computer cheats please. Once you find a bug/hack/cheat post it here and tell me how you bypassed it.[/left]

8543 posts
Posted 12 March 2013 - 01:06 PM
Open computer interface, hold ctrl-s until computer shuts down. Place floppy disk containing a blank file named startup in disk drive. Open computer interface. Security bypassed.

25 posts
Posted 12 March 2013 - 01:09 PM
You obviously tl;dr'd…. I quote:
[left]Note: You have to do it by code, no driver on the top of computer cheats please[/left]

8543 posts
Posted 12 March 2013 - 01:16 PM
That's not a cheat, it's code. It happens to be empty code, but the system was bypassed. This is not an uncommonly known thing.

25 posts
Posted 12 March 2013 - 01:19 PM
Either way I said no driver on top of the computer. So why do it? Could you not bypass it without using physical means?

1619 posts
Posted 12 March 2013 - 01:36 PM
Either way I said no driver on top of the computer. So why do it? Could you not bypass it without using physical means?
Put it on the front, back, left, right, or bottom. :P/>

73 posts
Location
Yes
Posted 12 March 2013 - 01:39 PM
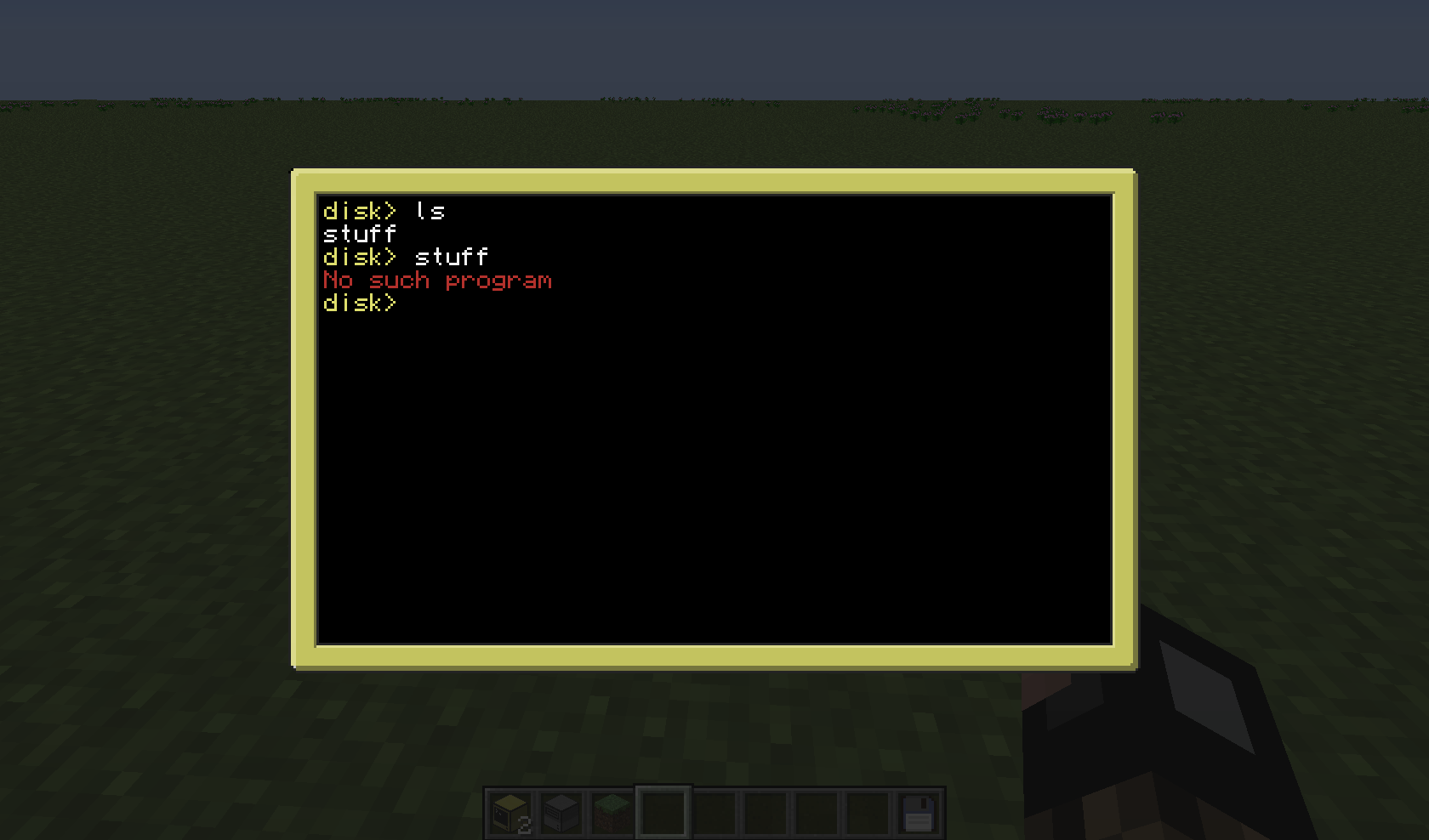
Something seems to be wrong with this program. I can't run files for some reason.
Spoiler

1688 posts
Location
'MURICA
Posted 12 March 2013 - 01:45 PM
Open computer interface, hold ctrl-s until computer shuts down. Place floppy disk containing a blank file named startup in disk drive. Open computer interface. Security bypassed.
If the program starts up from a disk drive on the top of the computer, it can't be bypassed using another disk.
Either on top or on bottom - I've tested this in 1.5(?) and it appears to load the disk on top before any other sides.
Though if you're able to place a drive, you'd be able to break one, so in the event that you can't bypass the system through physical means, simply blocking all sides of the terminal but one is considered secure.

892 posts
Location
Where you'd least expect it.
Posted 12 March 2013 - 01:54 PM
env=getfenv(1)
env.virtualDir="/"
env.iVirualDir=1
env.virtualDirCurrent="/"
setfenv(fs.delete,env)
fs.delete("disk/startup") --Unsandboxed :P/>/>
os.reboot()
Bypassed.
Also, main drive is on top.

25 posts
Posted 12 March 2013 - 02:10 PM
Something seems to be wrong with this program. I can't run files for some reason.
Spoiler

Thanks I will get to work on that immediately.

25 posts
Posted 12 March 2013 - 02:23 PM
Change Log V1.0.1
———————
+ I fixed the program not running feature.

25 posts
Posted 12 March 2013 - 02:31 PM
env=getfenv(1)
env.virtualDir="/"
env.iVirualDir=1
env.virtualDirCurrent="/"
setfenv(fs.delete,env)
fs.delete("disk/startup") --Unsandboxed :P/>/>/>
os.reboot()
Bypassed.
Also, main drive is on top.
That did not work :)/>
P.S. is Sphex's server down for you too?

892 posts
Location
Where you'd least expect it.
Posted 12 March 2013 - 03:17 PM
env=getfenv(1)
env.virtualDir="/"
env.iVirualDir=1
env.virtualDirCurrent="/"
setfenv(fs.delete,env)
fs.delete("disk/startup") --Unsandboxed :P/>/>/>/>
os.reboot()
Bypassed.
Also, main drive is on top.
That did not work :)/>
P.S. is Sphex's server down for you too?
?
Worked for me…
And its up now.

7508 posts
Location
Australia
Posted 12 March 2013 - 03:44 PM
That did not work :)/>
Looks like it should work.

25 posts
Posted 12 March 2013 - 04:05 PM
It didn't work in single player for some reason.

194 posts
Location
Spain
Posted 13 March 2013 - 06:02 AM
Either way I said no driver on top of the computer. So why do it? Could you not bypass it without using physical means?
The disk can be placed in the disk drive that the computer already has and it will work without breaking any rule.

8543 posts
Posted 13 March 2013 - 06:44 AM
The example code above needs to delete "/startup" in addition to anything else it deletes. All paths it goes after need to start with "/".

43 posts
Location
Germany
Posted 13 March 2013 - 07:52 AM
So the script you've posted is supposed to be the startup script of the computer, right? (/startup)
In that case all you need to do is:
disk>lua
lua>fs.open('../startup', 'w')
lua>os.reboot()
It's way too simple, guess I have done something wrong..

8543 posts
Posted 13 March 2013 - 07:54 AM
Yeah, his protection script does block naive attempts like that, at least.

43 posts
Location
Germany
Posted 13 March 2013 - 07:56 AM
Well, I've tried it and it works.

8543 posts
Posted 13 March 2013 - 08:28 AM
Does it? Now, that is interesting.

43 posts
Location
Germany
Posted 13 March 2013 - 09:08 AM
The ".." is messing up his sandbox code.

504 posts
Location
Seattle, WA
Posted 13 March 2013 - 01:55 PM
I bypassed your program. Look into lua's 'rawget' function to avoid a hole like this again:
Pastebin
link.
Code:Spoiler
--[[
Metatable Injection Trystan Cannon
12 March 2013
This script uses metatables and their
respective metamethods to inject into
functions that restrict certain actions
based on string values.
Using metamethods, we can bypass string
checks and cause certain flags to pass
even though we're using a metatable
rather than an actual string.
This is the function we'll be bypassing:
fs.open = function(path, mode)
path = shell.resolve(path);
if(mode == 'r')then
if(path:sub(1,13)=="rom/programs/")then
return fsOpen(path, mode);
end
end
if(path:sub(1,iVirtualDir)==virtualDir)then
return fsOpen(path, mode);
else
return fsOpen(virtualDirCurrent.."/"..path, mode);
end
return nil;
end
]]--
--======================================================================
-- Variables:
local targetPath = "/startup" -- The path of the file we want to get a handle on through the StringBomb.
local oldShellResolve = shell.resolve -- This is the old shell.resolve function that we need to replace in order to keep the path table given
-- to 'fs.open' to remain our table.
local virtualDirectory = "Not the virtual directory." -- This is the area where the program has sandboxed our code to. We want this to fail, by the way.
local StringBomb = { -- This is the table that the __index metamethod will be referencing for any functions invoked on our 'StringBomb' object.
-- When substring is called on this method, we want it not to return the virtual directory
-- the 'fs.open' method is looking for.
["sub"] = function (self)
return virtualDirectory
end,
-- When self:len() is called by our replaced shell.resolve function, we want it
-- to return -1 so that we can identify our table.
["len"] = function (self)
return -1
end
}
StringBomb.metatable = { -- The metatable for the StringBomb. This will allow us to sneak into the 'fsOpen' call when the virtual directory is concatenated with us.
__index = StringBomb,
-- When someone tries to concatenate a StringBomb with another string, then return
-- the target of the file we want to get in to.
__concat = function (firstOperand, secondOperand)
return targetPath
end
}
--======================================================================
--======================================================================
-- Function replacement:
-- Replace the 'shell.resolve' function so that our table, when passed to 'fs.open', will remain the same rather
-- than being a string.
shell.resolve = function (path)
if path:len() == -1 then
return path
end
return oldShellResolve (path)
end
--======================================================================
--======================================================================
-- Main:
-- Create the StringBomb object we'll use to get into the startup file.
local startupBomb = {}
setmetatable (startupBomb, StringBomb.metatable)
-- Get a file handle using our StringBomb.
local startupFileHandle = fs.open (startupBomb, 'w')
startupFileHandle.write ("print ('Startup accessed.')")
startupFileHandle.close()
-- Prompt the user that we have succeeded.
print ("Startup overwritten. Rebooting.")
sleep (0.5)
os.reboot()
--======================================================================
I used a metatable to change the nature of concatenation with my 'string bomb' in order to pass your test for the modded 'fs.open' function to call the native 'fs.open' at 'fsOpen' with "/startup" as the path.









