Enigma is a Simple to use encryption software made in order to ensure security of your programs on SMP servers. Multiple functions allow you to use it in the way you feel is best for you!
Encryption system is based of Military version of Enigma Machine.
I am trying to keep it as close to how original Enigma Machine worked as i can.
You can select 3 out of 10 predefined Rotors. You then select starting positions of said Rotors.
That gives 857375000 unique Rotor/Start Position combinations.
You can read more about it in http://en.wikipedia..../Enigma_machine
I have made few modification to it in order to be able to encrypt all common use symbols.
Download Here: http://pastebin.com/WYuNMxQx
Or ingame using command:
pastebin get WYuNMxQx enigmaFeatures List:
- Encryption/Decryption of strings
- 100% safe to your programs - no risk of corruption - if Enigma sees symbol it don't understands it simply writes it on without encryption.
--# create a new crypter
crypter = enigma.crypt(A,B,C,a,b,c)
--# A,B,C,a,b,c are starting positions on crypter.
--# where A,B,C are numbers 1-10 that tell enigma witch out of 10 standard rotors to use and a,b,c are numbers from 1-96 that set starting positions of said rotors.
--#A,B,C can also be a valid rotor tables.Valid rotor table is table containing numbers from 1-96 in random order.
--# encrypting string
ciphertext = crypter("plaintext")
--# duplicating crypter
crypterclone = crypter.copy()
--# to decrypt create crypter with same starting positions as one used to encrypt
decrypter = enigma.crypt(A,B,C,a,b,c)
decrypter(ciphertext) -> "plaintext"
--# to stop crypter from being able to be copied simply add true flag at end of attributes
nocopycrypter = enigma.crypt(A,B,C,a,b,c,true)
--# You can also stop duplication at later time by running
nocopycrypter.blockCopy()
Here is example program:
Spoiler
--# get command line arguments
tArgs={...}
--# load the enigma API
os.loadAPI("enigma")
--# create your crypter
local crypter = enigma.crypter(1,1,1,1,1,1)
--# copy it
local crypterclone = crypter.copy()
--# crypt first argument from command line and print it
local secret=crypter(tArgs[1])
print(secret)
--# decrypt it and print decrypted
local truth = crypterclone(secret)
print(truth)
Screenshot of that program in action:
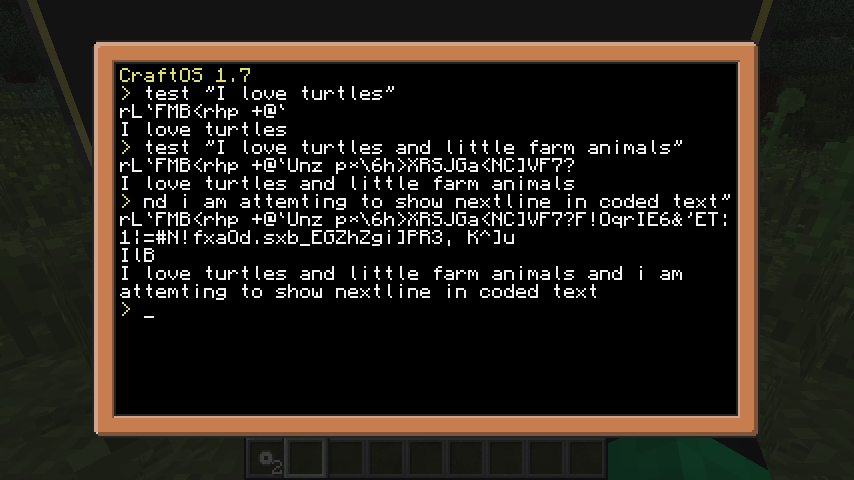
Notes:
- In case of A,B,C instead of using numbers 1-10 for standard rotors you can make your own and give it instead of the number. Rotor is table containing numbers from 1-96 in random order.
- Instead of loading enigma as API you can use it as file encryption program. Simply use "enigma <absolute path> and after few quick questions selected fill will be encrypted.
- Enigma was secure at time of its creation. In this days it is easy to brute force. This program was not made to be a secure encryptor instead it is a recreation of actual enigma method of encryption.
Spoiler
Enigma - Encryption Software For Your Programs v3Enigma is a Simple to use encryption software made in order to ensure security of your programs on SMP servers. Multiple functions allow you to use it in the way you feel is best for you!
Encryption system is based of Military version of Enigma Machine.
I am trying to keep it as close to how original Enigma Machine worked as i can.
You can select 3 out of 10 predefined Rotors. You then select starting positions of said Rotors.
That gives 857375000 unique Rotor/Start Position combinations.
You can read more about it in http://en.wikipedia..../Enigma_machine
I have made few modification to it in order to be able to encrypt all common use symbols.
Download Here: http://pastebin.com/NKhvzq2B
Or ingame using command:
pastebin get NKhvzq2B enigmaFeatures List:
- Encryption/Decryption of files
- Decryption and running programs from drive
- Creating Self-Decrypting Programs for fast usage.
- 100% safe to your programs - no risk of corruption - if Enigma sees symbol it don't understands it simply writes it on without encryption.
Spoiler
- enigma code [path] - Encrypt/Decrypt [path] file into [path].code file.
- enigma codein [path] - Encrypt/Decrypt [path] file into itself (overwrites content) file.
- enigma run [path] - Decrypt [path] file and run it. Effects on non coded file are undefined
- enigma exec [path] - Encrypt/Decrypt [path] file into [path].code file and add self-decrypting code. This file can be used without main Enigma file. Simply run it and enter Pass.
- Use enigma help or enigma ? for in-game Help-page
- Use enigma help2 or enigma ?2 for in-game Advanced Usage
Program is made to fit all 4 possible types of computer advanced or normal / turtle or computer no matter
Code Entering GUI Will change itself in order to fit your Needs.
Side Features include:
- Ability to Hide/Show numbers you are entering
- Full touchscreen Control on Advanced Computers/Turtles
- Ability to enter Basic Mode - Simple menu that uses print() and read()
Spoiler
In this example i am assuming you are creating self-decrypting file froma hello file you have on your disk.
- enigma exec [path] - where [path] is absolute path to hello file
- You will see one of 4 Screens Depending on Machine you are running this program on. Now you select from 10 Rotors you want to use. You can use same Rotor more than once. Then you enter starting positions of rotors. Remember all 6 numbers. For More info about Rotors and how they work see: http://en.wikipedia...._machine#Rotors
- Now you will have hello.code file in same directory as hello file. Thats Self-decrypting program you created. You can rename it and move it wherever you need it.
- Remember to hide unencrypted hello to somewhere safe - you don't want anyone getting this one do you? :P/>
- When you run hello.code file you will see familiar Rotor Setup Screen. Enter Same Rotors and Starting positions in order to begin encryption. After you enter it hello program will be decoded and run.
- Thats it! Tx for read and hope you like this program.
Change-log:
Spoiler
v0.9 - Initial Release on Ask A Pro Sub-forumv1.0 - Release On Programs Sub-forum - Added Turtle detection codes and 2 bug fixes
v2.0 - Ability to select 3 rotors from selection of 10 like in Basic Military version of enigma
v3.0 - Fixed up run string command using my new knowledge
Plans For Future:
Spoiler
v3.5 - Clean Up Code :D/>v4.0 - Implementation of Plugboard from Navy Military version of enigma in form hidden of .plugboard file
v5.0 - Encrypting files in mass,encrypting Directories.





