Obsoleted by Enchat 3. Go there instead.
Enchat is a simple-to-use encrypted, decentralized, and colorized chat program for computers (both normal and advanced.)
It has commands, and you can scroll through the chat log with the mouse wheel.
Color formatting is supported, with '&' for text and '~' for background. This is configurable.
While entering text, your message will automatically color-format as you type it. This is also configurable.
pastebin get JtgbWdV5 enchat2
std pb JtgbWdV5 enchat2
When you boot it up, enter an encryption key to use, then your name. Both can also be inputted as arguments, too. Make sure to make your name colorful!
Press PageUP or PageDOWN to scroll up or down 4 lines. This is, as are other things, configurable.
If you have Enchat 2.3 or later installed on a Neural Connector with the Overlay Glasses (and a wireless modem), then you can get notifications for messages in the topleft corner of the screen. It's even kerned properly, woah.
Syntax:
enchat2 [key] [name]
Command list:
Spoiler
'/help [command]'
Returns a list of all the commands. If [command], then gives a small description of the command.
'/update ["beta", "stable"]'
If running from shell: downloads Enchat from pastebin, replaces current program, then reruns.
If running from dofile: prompts for download path, then downloads from pastebin, and reruns.
If pastebin is inaccessible, or is whitelisted for some reason, or if Enchat is in a read-only directory (/rom), it will safely go back to the chat prompt rather than crashing.
If you give the argument "beta", will update from the beta URL. Don't do that, though.
'/cry'
Returns a list of all users in range using the same key as you.
'/heil <person>'
Heil someone. If an argument isn't given, it defaults to a random name.
'/me <text>'
Make a message in the format of <*> %yourname% %text%. Just like in regular minecraft!
'/clear'
Clears your inventory. Just kidding. It actually steals your girlfriend.
'/ping [text]'
Pong!
'/whoami'
Tells you your current nickname.
'/colors'
Lists all color codes for use in text formatting. Use '&' to change text color, and '~' to change background color.
'/nick <newname>'
Changes your nickname. You can even use color formatting in your name! Maximum 20 characters, after formatting.
'/palate <element> <newColor>'
Change the color palate of various elements of the interface. Currently, it's the following:
text, chattxt, bg, chatbg
'/set [configOption] [newValue]'
Change a config option for the current session, such as the scroll distance of the Page keys, whether or not text is colorized, whether to reverse scrolling direction, etc.
'/exit'
Closes out of Enchat cleanly.
Screenshot(s):
Spoiler
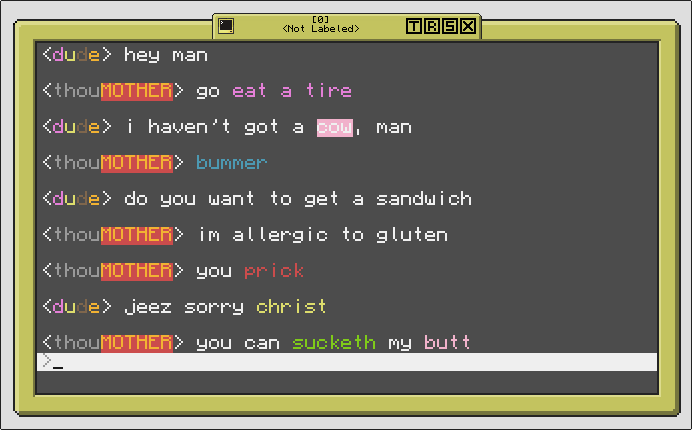
Colorful names and messages, and all encrypted with AES! (apparently it's "don't have a cow, man" but whatever)
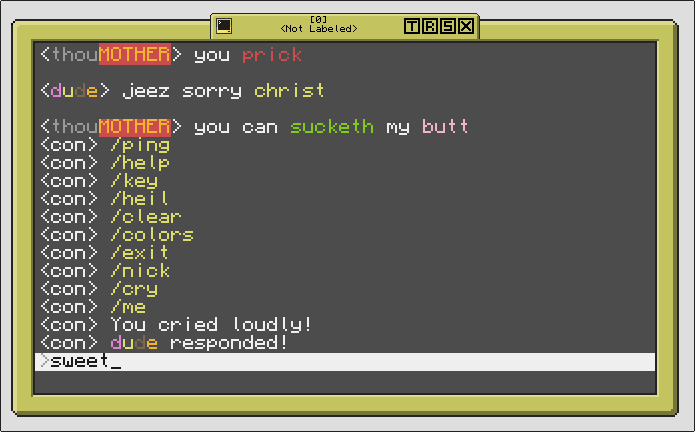
Up to *that* many commands, and more since version 2.2!
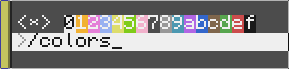
List all colors for a quick reference!
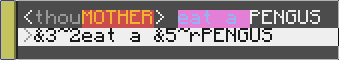
Make very colorful messages (fancyMsg = true by default, but here it's false)
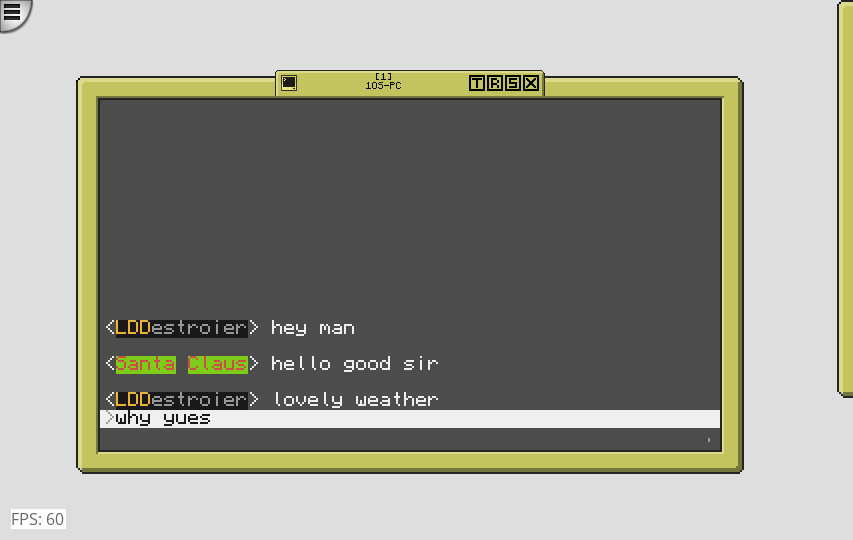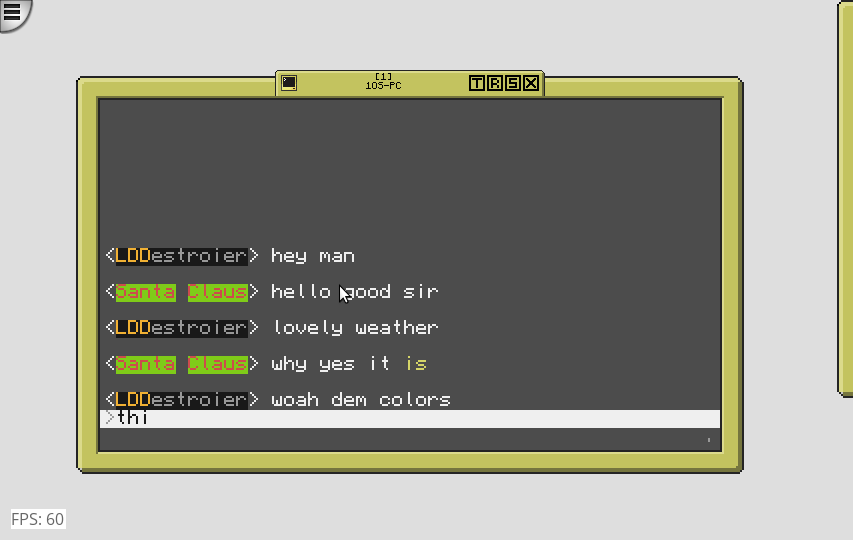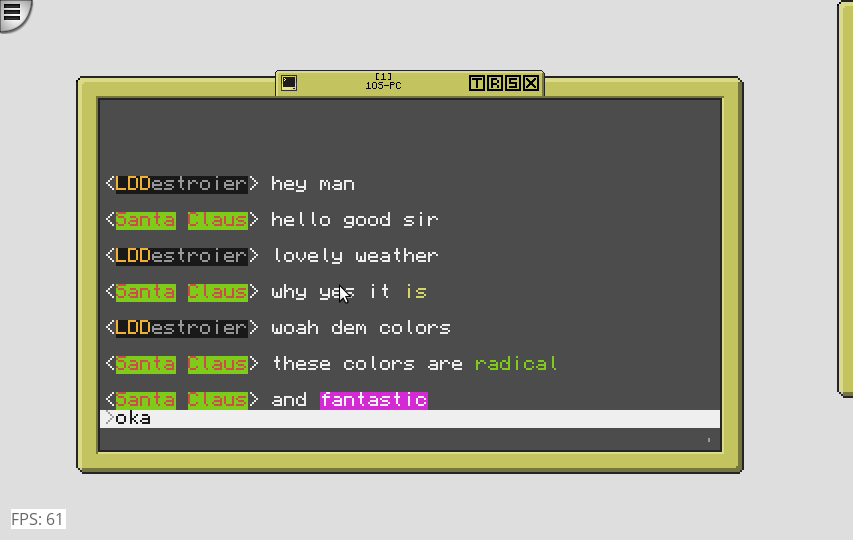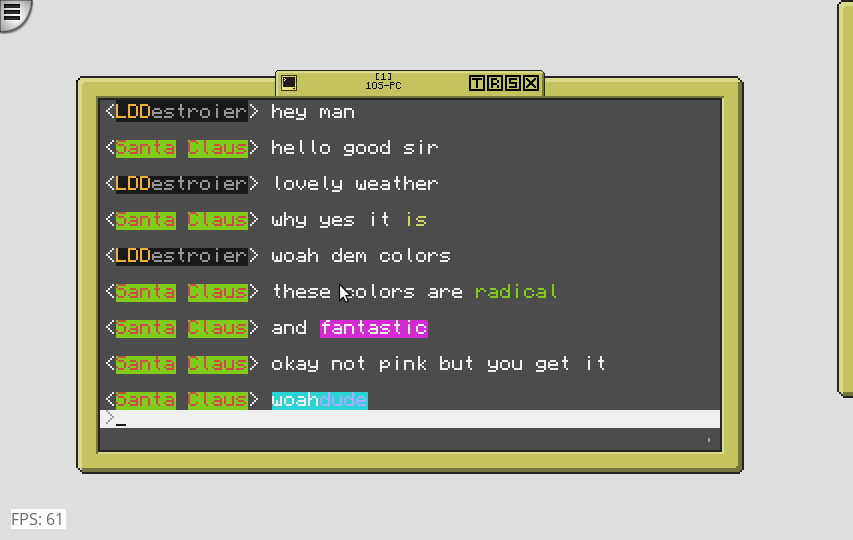
Format colorful dialogue as it's being typed! No other chat program does this to my knowledge! Which arguably isn't saying much
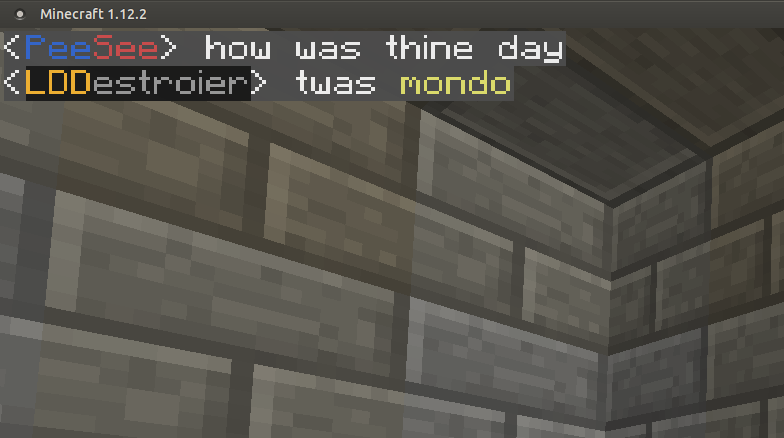
With the power of Plethora's Overlay Glasses, you can get screen notifications for messages in Enchat! They last 10 seconds onscreen by default, and can be disabled with the /set command.
You can get this with SuperTextDownloader! Contract it here!
Enchat requires ComputerCraft 1.6 (Minecraft 1.6.4) or later. I have yet to thoroughly test it, but based on when each function was added according to the CC wiki, you should be fine.










