
749 posts
Location
BOO!!
Posted 24 March 2018 - 02:48 AM
local fenv = getfenv(load)
fenv._G = fenv
fenv.error = function() end
setfenv(load, fenv)
load(string.dump(function() print("HI") end), "X", "b", _G)()
This shouldnt work…
Edited on 26 March 2018 - 02:13 PM

2427 posts
Location
UK
Posted 24 March 2018 - 12:58 PM
b flag in
load function is for binary chunks, which
should be blocked by the bios
What version of CC is this, have you replicated the issue on latest?
Edited on 24 March 2018 - 11:59 AM

1426 posts
Location
Does anyone put something serious here?
Posted 24 March 2018 - 03:03 PM
b flag in
load function is for binary chunks, which
should be blocked by the bios
Eh. It doesn't actually validate that elsewhere, so you can still load binary flags by passing nil. Given that CC runs LuaJ instead of PUC Lua, it's really not a big issue - you can't actually exploit bytecode at all.

749 posts
Location
BOO!!
Posted 24 March 2018 - 09:53 PM
Here is the best proof I can give:
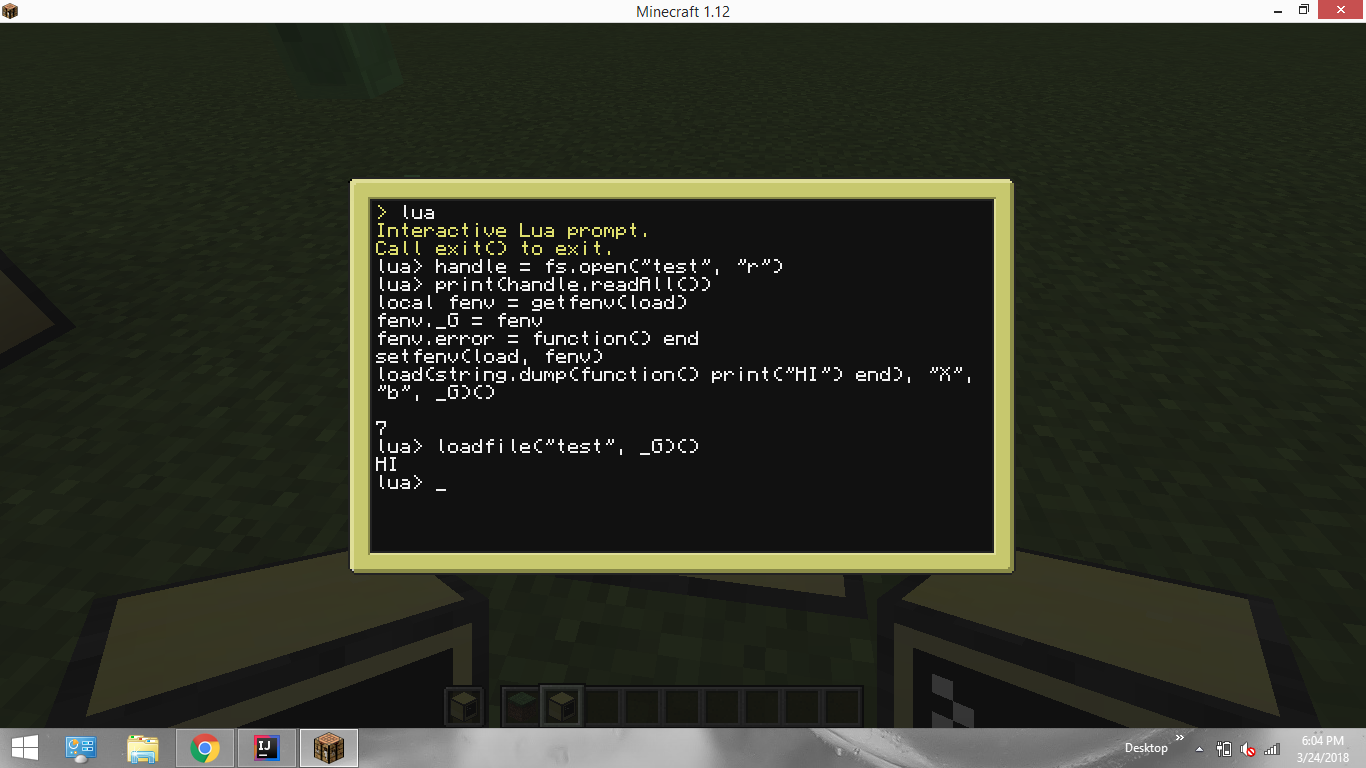
Though I cannot show you that I have not modified the environment, you can try it for yourself.
BTW, you can't actually exploit bytecode at all.
Obfuscated downloads are not allowed.
Bytecode exploit: write a script that deletes all files, compile it to bytecode, base64 it, write what appears to be an installer, de-base64 it at runtime, and pass the result into the hacked load.
Edited on 25 March 2018 - 12:20 AM

749 posts
Location
BOO!!
Posted 25 March 2018 - 12:01 AM
More "correct" version of the code that will not override the global env. The previous code still shows the point, but was not 100% correct.
local fenv = {}
for k, v in pairs(getfenv(load)) do fenv[k] = v end
fenv._G = fenv
fenv.error = function() end
setfenv(load, fenv)
load(string.dump(function() print("HI") end), "X", "b", _G)()
Previously _G.error would be overrided, this still shows the point without doing that.
Edited on 24 March 2018 - 11:02 PM

1610 posts
Posted 26 March 2018 - 04:17 PM
you can't actually exploit bytecode at all.
Obfuscated downloads are not allowed.
Bytecode exploit: write a script that deletes all files, compile it to bytecode, base64 it, write what appears to be an installer, de-base64 it at runtime, and pass the result into the hacked load.
That's not really an exploit, and regardless, you can do that with source code to the same effect.

749 posts
Location
BOO!!
Posted 26 March 2018 - 04:18 PM
But still, I would think there would be a point to the (rather badly coded) load wrapper
Also, bytecode is still further from readable then source code. Plus, if you convert the hard-to-read source code to bytecode, it's even harder to read.
Edited on 26 March 2018 - 02:20 PM

463 posts
Location
Germany
Posted 30 March 2018 - 06:04 PM
Bytecode exploit: write a script that deletes all files, compile it to bytecode, base64 it, write what appears to be an installer, de-base64 it at runtime, and pass the result into the hacked load.
Or, instead of doing that, you could just delete all files in the installer script. Maybe add 200 whitespaces in the first line and after that the malicious code in the same line so noone will know.
That's way sneakier than de-base64-ing some string and loading it.





